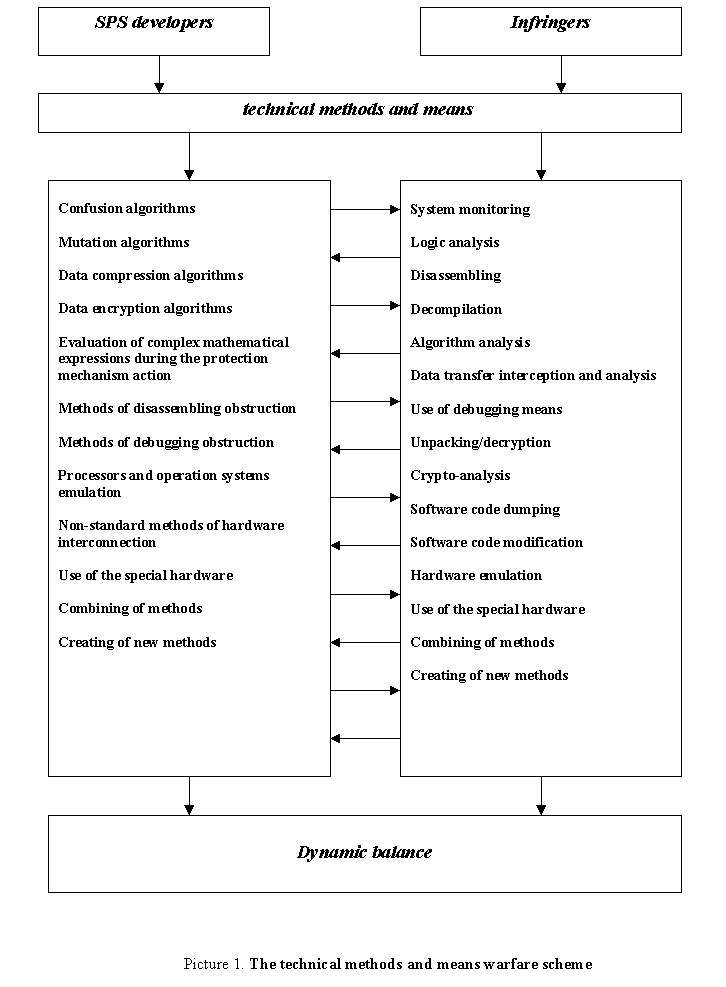
There is a complex of questions covered in this report related to the research of software protection systems. The analysis of existing means and methods of software protection is carried out. There is a set of criteria developed and offered for the software protection systems efficiency estimation.
Software protection systems are widely spread and are in continuous development, due to the expansion of the software and telecommunication markets. The necessity of use of software protection systems (SPS) is caused by a number of problems. The most important of them being: illegal use of algorithms, that are the intellectual property of the author, in creating of analogues and derivative works of a product (industrial espionage/plagiarism); unauthorized use of software (theft and copying); unauthorized software modification with the purpose of inculcation of malicious code; illegal software distribution and selling (piracy).
We can classify all existing software protection systems by a number of attributes and namely: installation method, protection mechanisms used and the functioning principle.
Software protection systems could be divided by the installation method into the following: systems being installed on compiled software modules; systems that are built in the software source code before compilation; and combined systems.
The systems of the first type are the most convenient for the software
manufacturer, as it is very easy to protect software which is completely ready
and tested (usually the process of installation of protection is automated as
much as possible and is reduced to the indication of the filename of protected
software and pressing "Enter"), that is why they are the most popular.
At the same time the resistance of these systems is relatively low (depending on
the principle of SP function), it is enough to determine the work end-point of
"protection envelope" where the control is passed to the protected
program, and then manually dump it in the unprotected form for revealing of the
protection.
The systems of the second type are inconvenient for the software manufacturer,
due to the necessity of training for the staff to work with the application
program interface (API) of the protection system with time and money expenses,
resulting from all of it. Besides that, the process of software testing becomes
complicated and program reliability goes down, because except the software
itself bugs could be in the protection system's API or in the procedures using
it. However, such systems are more resistant to attacks since the clear border
between SPS and software disappears here.
The most robust are combined
protection systems. With pros and cons of the systems of the second type, they
greatly obstruct the analysis and deactivation of their own algorithms.
It is possible to classify SP by protection mechanisms used as follows: systems, using complex logical mechanisms; systems, using crypto-protection of the software; and combined systems.
The systems of the first type use various methods and tricks, oriented to
the obstruction of disassembling, debugging and analysis of algorithms of SP
and protected software. This type of SP is the least resistant to attacks,
since for the revealing protection it is enough to analyze the logic of checking
procedures and to modify them appropriately.
The systems of the second type
are more stable. It is necessary to determine the software decryption key for
deactivation of such a protection.
The most attack-resistant are combined
systems.
There is a set of methods for software protection used, such as:
At the same time, infringers also use a set of methods and means for SPS
breakage. The situation of warfare between SPS developers and infringers is
being constantly changed by the combining of the already known defense and
offense methods as by invention and applying the new ones.
In general this
interaction can be described by the scheme in Picture 1.

It is possible to subdivide SPS by the functioning principle into the following: packers/encryptors; unauthorized copy protections and unauthorized access protections.
Initially the main goal of packers/encryptors was to reduce the executable module size on the hard disk without any harm for the functionality of the program but later the aim of software protection against analysis and modification came on the first place. There are used data compression algorithms, tricks related to the use of undocumented OS and processors features; data encryption, mutation algorithms, confusion of program logic, putting the OS in unstable state during software execution and so on in order to achieve it.
Positive Sides:
Negative Sides:
Unauthorized copy protection systems "tie up" the software to the distribution volume (floppy disk, CD, etc.). Given SPS type is based on deep understanding of drive controllers functioning, their physical parameters, non-standard formatting, reading/writing modes, etc. In this situation a distribution volume on the physic level is being created, which (supposedly) has some unique qualities (usually it is achieved by non-standard volume formatting and/or writing on it some additional information, it could be a password or label or a part of the program, etc.) and on the program level a special module is being created which is tuned up for identification of the protected volume by its unique characteristics. Packers/encryptors tricks are also applicable to these systems.
Positive Factors:
Negative Factors:
Unauthorized access protection systems implement preliminary or periodic authorization of the software user or his computer system by querying some additional information. We can ascribe to this type of SP such systems as password protections, systems binding themselves to user's computer, systems with key disks and hardware lock protections. In first case key information is used to be entered by the user, in second case it is contained in the unique parameters of user's computer system, in third case it is on the key disk and in fourth, the key information is stored in the hardware key's chip.
This class of SPS is the most commonly used now. The main principle of such systems function lies in the identification and authentification of the software user by querying additional data. It could be a firm title and/or user's first and last name along with his password or just a password or registration code. This information could be asked in various situations, for example, at program start or after the end of a trial period, within registration procedure or during software installation. Password protection procedures are relatively simple in realization, that is why they are used by software vendors so often. The majority of password SPS's use logic mechanisms coming to password/code validation and granting or denying of software execution depending on the validation results. There also exist systems, which cipher software being protected and use the password or value produced from it as a deciphering key. Most of such systems use weak or simplest ciphers irresistible for direct attack. It happens due to complexity of the correct realization of highly resistant ciphers and independence of their use for protection of low and middle-cost shareware products, which form the main part of the software that uses password protections. Only in recent time there were developed password SPS's with realizations of durable crypto algorithms such as DES and RSA. Such SPS are released as a standalone protection modules or special libraries being embedded into software.
The weak point of password protections is in the password validation block. For such validation is possible to compare entered password with the right one stored inside the program or correctly generated from the information entered by user. It is also possible to compare derivative values produced from an entered and valid passwords, for example hash-function. In such case it is reasonable to store in the program only the produced hash-values for strengthening of SPS resistance. It is possible to reveal the real password stored inside a program, to find correctly generated password or create a program to brute-force password corresponding to given hash-sum by means of validation routines analysis. Besides that, if the SPS doesn't use cryptography it will be enough just to modify validation logic to compromise the protection. Ciphering systems are more durable to attacks but the use of simple or weak ciphers creates a threat of decryption.
There exists a threat of password input interception for all password protections. In addition to that, most of SPS's use password validation only once, usually during the software installation, after that SPS simply gets disabled, that creates a threat of unauthorized software copying.
Positive Sides:
Negative Sides:
Systems of that type implement the search or creation of unique signs of the user's computer system during software installation. After that, protection module inside the software is being tuned up for this signs, according to which there will be detected unauthorized use of the software. It is possible to use techniques of processor, motherboard, peripherals or OS parameters validation, flash memory reading/writing, creation of hidden files, tuning for common RAM usage map, etc.
The weak point of such systems is that the software always runs at user's PC, which provides an opportunity of process dumping after protection finishing, protection reversing and authentification data exposing.
Positive Factors:
Negative Factors:
This class of SPS gets an increased popularity during the recent time among the software developers. Under "hardware lock" here we mean a protection system based on the use of hardware keys. Hardware key is the hardware part of SPS and is a boxed board equipped with memory and, in some cases, with microprocessor and adapted for one of the standard PC ports (COMM, LPT, USB, etc.) or motherboard extension slots. SMART-cards could also be used as such a hardware key. According to the carried out research hardware lock SPS's are one of the most durable protection systems at present time.
By the architecture all hardware keys could be subdivided into keys with memory (without processor) and keys with microprocessor (and memory).
The least resistant (depending on the program part type) are the systems with hardware keys of the first type. In such systems the critical data (decryption key, jump table) is stored in the key's memory. For deactivation of such protections infringer needs the hardware part of SPS (the main technique is in interception of the dialog between software and hardware parts of SPS to gain access to critical information).
The most resistant are the systems with keys of second type. Such complexes contain in their hardware part not only the decryption key but cipher/decipher program so during the SPS work hardware key receives encrypted data and sends back decrypted one. It is difficult enough to intercept the decryption key in such systems because all operations are performed by the hardware. However, there remains the possibility of program dumping and hardware emulation. Besides that, cryptology methods are also applicable for such systems.
Positive Factors:
Negative Factors:
In present time systems of that type are relatively rare because of their obsoleteness. Given systems generally are analogous to hardware lock SPS but here the critical data is stored on the special key volume. Also, there are many common points with copy protections because they use the same techniques.
The main threat for such systems is the critical information read interception along with unauthorized copying of the key volume.
Pros and cons of this SPS type almost completely repeat the ones of hardware lock SPS:
Positive Factors:
Negative Factors:
It is necessary to say that users directly feel only negative side of SPS. But software developers consider only that pros and cons, which have relation to themselves and practically don't care about parameters related to the end-user.
By the results of the research the set of applicability indices and evaluation criteria was provided.
SPS correspondence to software developer's functional requirements and software resistance requirements; software and SPS system requirements; software and SPS sizes; software functional direction; availability and type of SP in analogues software products - competitors.
Correlation between piracy loses and the main profit value; correlation between piracy loses and the cost of SPS and its introduction; correlation between software and SPS prices; accordance the cost of SPS and its introduction to established goals.
Prevalence and popularity of the software; software use and distribution conditions; rareness of the software; presence of threats; probability of user into infringer transformation; the role of documentation and support in software exploitation.
Impediment of illegal copying and illegal access; monitoring protection; absence of logic vulnerabilities and system realization errors.
Using of standard mechanisms; new/non-standard mechanisms
Probability of protection failure (unauthorized access); average time of safe work; probability of SPS crash, average time of work without crashes, frequency of false alarms.
Use of undocumented features; "virus" technologies and OS holes.
Absence of conflicts with system and application software; absence of conflicts with existent hardware; maximal compatibility with future versions of software and hardware.
Need and complexity of additional SPS configuring; documentation availability; availability of information on SPS fixes due to bugs/incompatibility/vulnerability; availability of service packs, safety of network transmitting of the password/code; delay due to physic transfer of password/key; consumer rights abuse.
Traffic overload (LAN licences); denial of service; slowing down of protected software; slowing down of OS work; usurpation of system resources; RAM overload; OS stability infringement.
Cost/effectiveness; cost/price of protected software; cost/eliminated loses.
True advertising; availability of independent expertise results; availability of side effects information; full information about SP for the end-user.
In general, the main scheme of software market agents interaction could
be described by Picture 2.
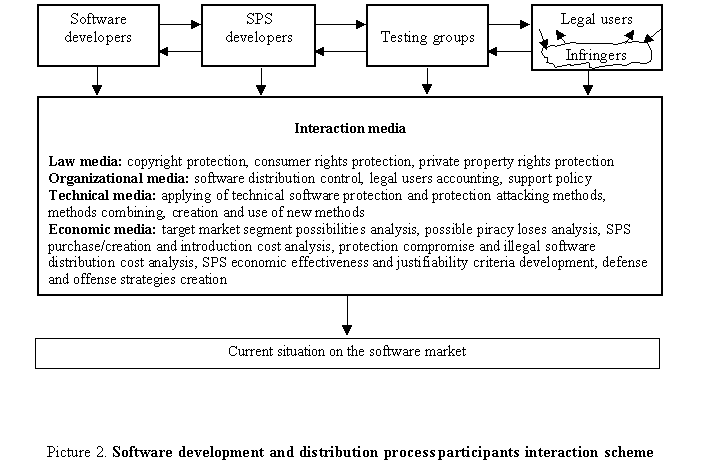
Within four interaction media types specified above the protecting side can (partly) control three of them: organizational, technical and economic media. However, it possible to lobby some desired laws too but we want to examine the most common case.
On our opinion, the most important interaction media is the economic media, since economic interaction, in this instance, is the prime cause and the aim of the whole interaction. Thus, the organizational aspect goes to the second place and the technical aspect goes to third one. It seems to us that today's software developers pays little more attention to some technical qualities of software protections than it should be. While developers seek for the most resistible protection they often forget about market analysis, software quality evaluation, competitive products, end-user's consumer rights, organization of software distribution, etc.
For example, the main aim of 'Warez' market is to fill the gap forgotten by marketing services of software developers. The majority of popular CAD/CAM and 3D Graphic Design and Animation software was positioned as a product for corporate users while these types of programs are quite popular between individual customers. Due to this mistake there wasn't done a clear price differentiation to attract individual buyers. It means that product prices are usually too high for private persons which makes them to steal software and support 'Warez' market. The situation is analogous on the international software markets, there is almost no price variations in different countries. Thus people from countries with lower average personal income would prefer to use 'Warez' instead of legal software.
We consider that attention to economic and organizational aspects of software distribution could reduce the pressure on the technical means of software protection along with piracy loses. It doesn't mean that we should abandon software protections, it means that the approach should be more systematic, complex and flexible.